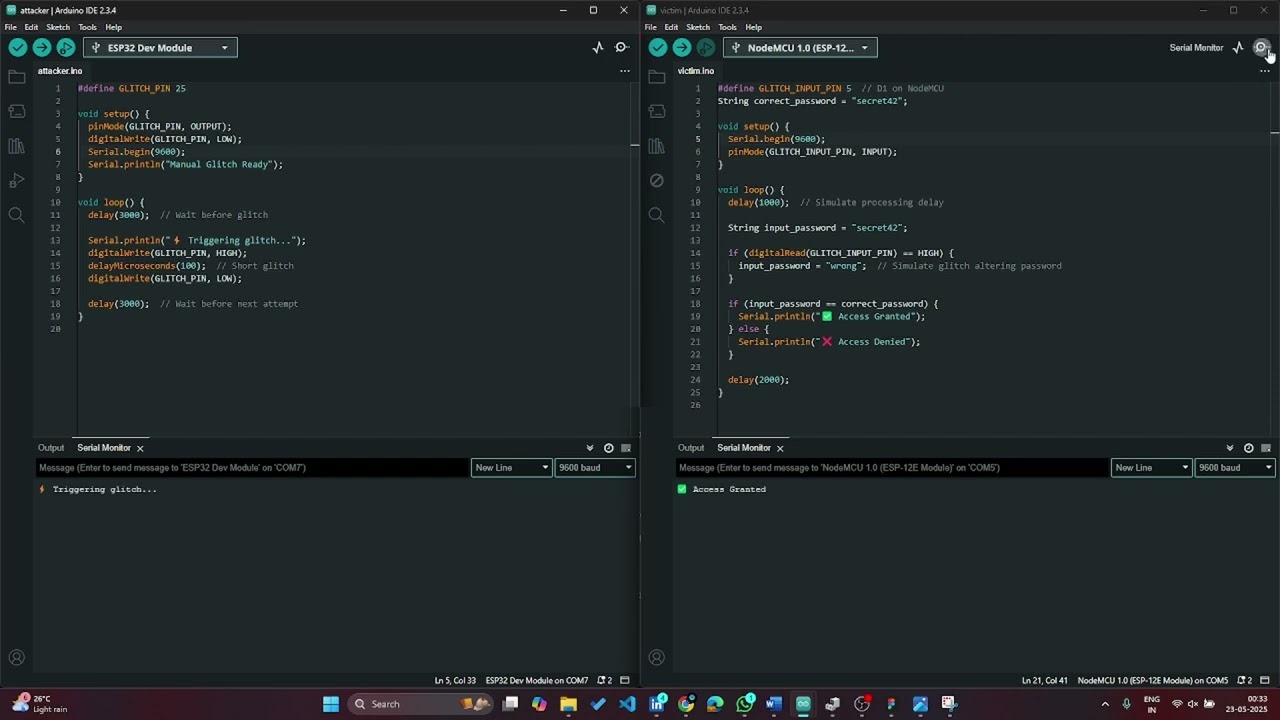
This project demonstrates a hardware-based voltage glitching attack using an ESP32 to bypass authentication on an ESP8266 by momentarily disturbing its power supply at precise moments — simulating real-world fault injection exploits.
| Component | Role |
|---|---|
| ESP8266 | Victim — runs password-check logic |
| ESP32 | Attacker — injects glitches via GPIO |
| Laptop | Monitors UART output and controls logic |
- ⏱️ Timing-based glitch trigger
- ⚡ Voltage fault injection (software controlled)
- 🔓 Bypass authentication logic
- 📟 Real-time serial monitoring
- 🧪 Modular for adding more side-channel or fault-based exploits
- 1 × ESP32 Dev Board
- 1 × ESP8266 NodeMCU (or equivalent)
- Common GND connection
- Jumper Wires
| ESP32 (Attacker) | ESP8266 (Victim) |
|---|---|
| GPIO (Glitch) | VCC / EN pin |
| GND | GND |
Note: Use a common ground between both devices.
- ESP8266 waits for a password input.
- ESP32 triggers a power glitch at a precise time.
- This disrupts a conditional check inside the ESP8266 firmware.
- If the glitch is timed right, authentication is bypassed.
- ESP32 controls the glitch via a GPIO pin
- That pin is connected to the EN pin or VCC line of the ESP8266 (use a series resistor for safety)
- Common ground between ESP32 and ESP8266
- Serial connections for monitoring both boards independently
-
Startup:
- ESP8266 initializes and waits for a password over Serial
- ESP32 is idle until triggered
-
Trigger:
- ESP8266 reaches password check stage
- ESP32 either listens for a specific signal or delays for a precise window
-
Fault Injection:
- ESP32 sends a fast LOW pulse to the EN or VCC of ESP8266
- This temporarily browns out the CPU without a full reboot
-
Result:
- If the glitch is timed right, ESP8266 skips or corrupts the password check logic
- Serial shows access granted without correct password
- Victim and attacker both output logs over USB serial.
- Use baud rate:
9600or115200(depending on code) - Use any serial monitor (Arduino IDE, PuTTY, minicom)
⚠️ This project is for educational purposes only. Unauthorized tampering with hardware may be illegal or violate terms of use.