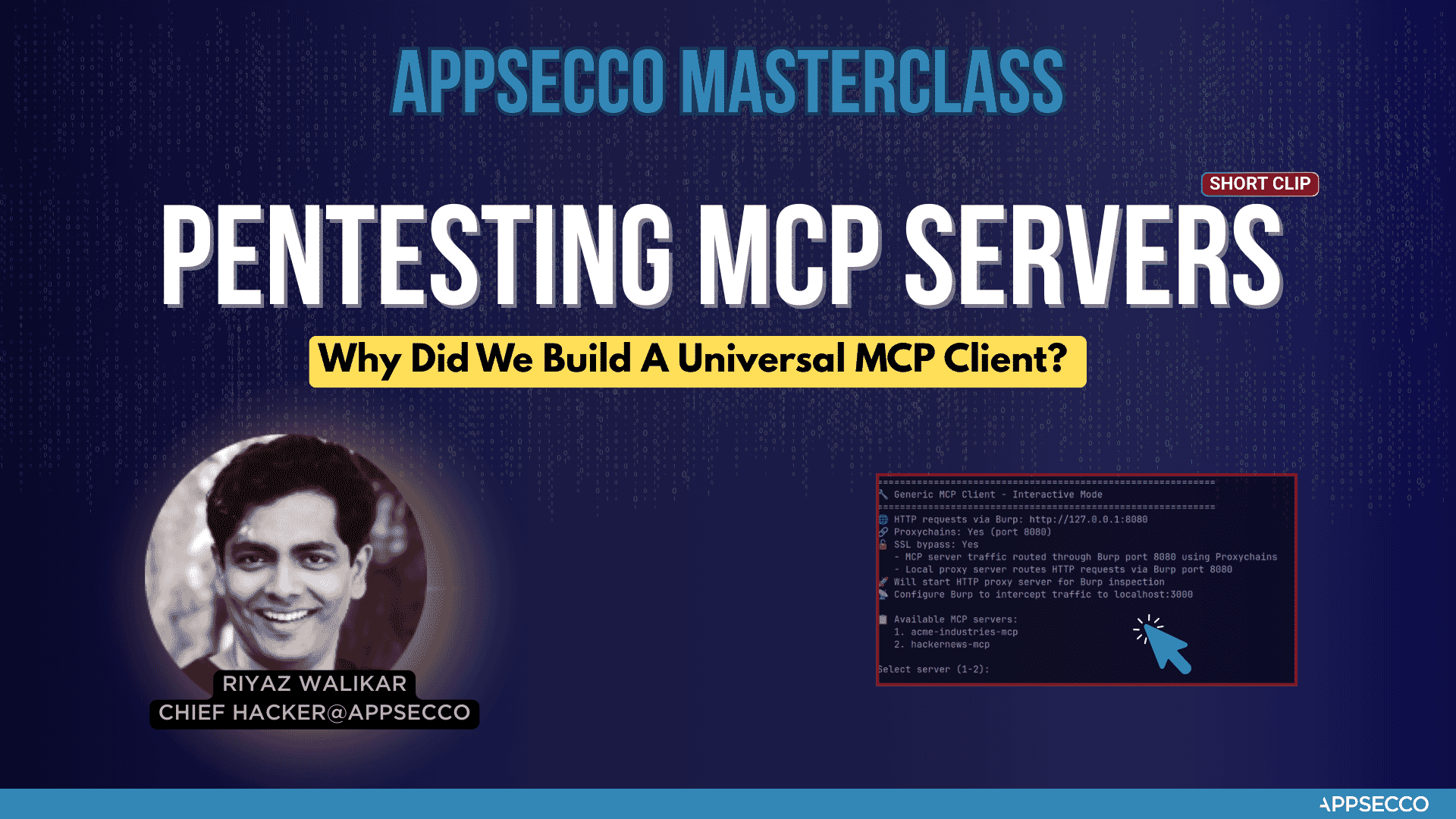
Semi Professional Security Tool with Cool Vibes - Send MCP Server Traffic to your Burp Suite
- 🔍 Advanced MCP Server Integration - Connect to any MCP server with professional-grade reliability
- 🌐 Enterprise Proxy Support - Seamless integration with Burp Suite and other security tools
- 🔗 Proxychains Integration - Professional traffic routing and analysis capabilities
- 🛡️ SSL Bypass Support - Advanced testing scenarios with certificate handling
- 📊 Interactive Security Testing - Professional interface for security assessments
The Appsecco MCP Client and Proxy is a professional security testing tool that provides:
- Local Relaying Proxy - Start a local proxy server to route traffic through Burp Suite or other security tools
- MCP Server Integration - Connect to MCP servers defined in
mcp_config.jsonand interact with their tools - Professional Traffic Analysis - Route all traffic through configurable proxies for security testing
- Enterprise-Grade Reliability - Built for professional security teams and penetration testers
- Python 3.7+
- Proxychains (for advanced proxy routing)
- Burp Suite (recommended for traffic analysis)
# 1. Create virtual environment
python3 -m venv venv && source venv/bin/activate
# 2. Install requirements
pip3 install -r requirements.txt
# 3. Run the professional security testing tool
python3 app.py --start-proxyThe tool will automatically detect if proxychains is installed and provide installation instructions if needed:
- Ubuntu/Debian:
sudo apt-get install proxychains - CentOS/RHEL:
sudo yum install proxychains - macOS:
brew install proxychains-ng
# Start with HTTP proxy server for Burp inspection
python3 app.py --start-proxy
# Use custom configuration file
python3 app.py --config my_mcp_config.json --start-proxy
# Disable Burp proxy routing
python3 app.py --no-burp
# Disable proxychains
python3 app.py --no-proxychainsusage: python3 app.py [-h] [--config CONFIG] [--proxy PROXY] [--start-proxy]
[--proxy-port PROXY_PORT] [--no-burp] [--no-proxychains]
[--no-ssl-bypass] [--debug]
Appsecco MCP Client and Proxy - Professional Security Testing Tool with proxychains support
options:
-h, --help show this help message and exit
--config CONFIG, -c CONFIG
MCP configuration file (default: mcp_config.json)
--proxy PROXY, -p PROXY
Burp proxy URL (default: http://127.0.0.1:8080)
--start-proxy Start HTTP proxy server for Burp inspection
--proxy-port PROXY_PORT
HTTP proxy server port (default: 3000)
--no-burp Disable Burp proxy routing
--no-proxychains Disable proxychains usage
--no-ssl-bypass Disable SSL certificate bypass
--debug Enable debug output for troubleshooting
Example: python3 app.py --start-proxy
Brought to you by Appsecco - Product Security ExpertsWhen using the --start-proxy flag, the tool creates a professional security testing environment:
1. 🚀 Run the app: python3 app.py --start-proxy
2. 🔧 MCP Server Starts with proxychains
3. 🌐 Local Proxy Server Starts on port 3000
4. 📡 App sends requests -> Local Proxy (port 3000) -> Burp (port 8080) -> MCP Server (stdio)
5. 🔗 MCP server via proxychains and Burp sends/receives data from backend server
6. 📤 MCP Server responds -> Local Proxy -> Burp -> App
- Launch Burp Suite and set it to listen on port 8080 (localhost)
- Configure Burp to intercept traffic as usual. This traffic will be travelling to
localhost:3000and backend APIs - Use Burp's professional tools like Repeater, Intruder, and Scanner
This tool includes anonymous usage analytics for Appsecco to obtain usage metrics
What we track: startup arguments, tool start and end, count of MCP servers, error rates and basic system info (OS, Python version)
What we DON'T track: Personal data, URLs, testing targets, traffic, credentials
Opt-out: Use --no-analytics flag or set MCP_ANALYTICS_DISABLED=true
Appsecco is a leading cybersecurity company specializing in product security testing, penetration testing, and security assessments. At Appsecco we hack your product and Cloud/K8s infra like hackers do. Real security testing for business-critical applications.
We wrote this MCP Client and Proxy tool when we had to testing the security of MCP server of a Fortune 500 FinTech company. It worked well for our Burp Suite workflow. We felt that there could be others who may need this as well.
Appsecco provides comprehensive cybersecurity services:
- 🔍 Penetration Testing & Security Assessments for Business-critical Products
- 🛡️ Application Security Testing
- 🏗️ Infrastructure Security Audits
- ☁️ Cloud Security Assessments
While this tool is offered under an open source MIT license, if you are interested in taking a look at our services. Here are the details.
- 🌐 Website: https://appsecco.com
- 📧 Email: [email protected]
- 📱 LinkedIn: https://linkedin.com/company/appsecco
This project is licensed under the MIT License - see the LICENSE file for details.
Built with ❤️ by Riyaz & Akash for the cybersecurity community.
Appsecco - Let Us Hack Your Product Like Attackers Do 🛡️