-
-
Notifications
You must be signed in to change notification settings - Fork 34
Description
What are the subjects of the phishing (domains, URLs or IPs)?
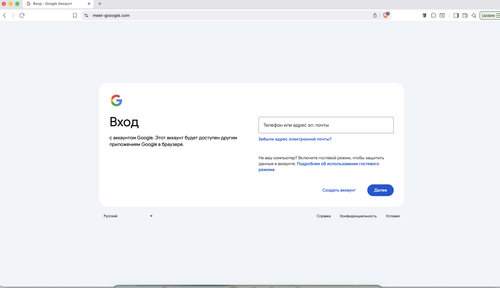
meet-gooogle.com
What are the impersonated domains?
meet.google.com
Where or how did you discover this phishing?
I discovered this phishing as part of an internal incident investigation after one of our employees reported a suspicious meeting invite received via Telegram. The message contained a link which appeared to be Google Meet but led to the phishing domain meet-gooogle.com; the attacker later edited the Telegram message and replaced the link with the real meet.google.com (the message shows an “edited” label).
During our investigation we found that credentials submitted to the fake page were used to initiate an OAuth link to a third-party service (Bybit); this activity was visible in our Google Workspace audit logs, which show login/OAuth events from suspicious IPs (recorded in our logs) and timestamps. We captured the page source (showing socket.emit('passwordSubmitted', ...)), WHOIS (recent registration), screenshots of the phishing landing, and a VirusTotal record confirming detections.
Do you have a screenshot?
Related external source
- https://www.virustotal.com/gui/url/53686a1ac702d5f1a2d3d897d9aaa905ca83e75a5c38804997c0377bae5278b1
- https://mxtoolbox.com/Problem/Blocklist/SEM-FRESH/?page=prob_blocklist&ip=meet-gooogle.com&link=button&action=blocklist:meet-gooogle.com&showLogin=1&hidetoc=1&reason=127.0.0.2
Additional Information or Context
We reported the domain to the registrar/host (Dynadot / Cloudflare) and to security vendors (Kaspersky, Dr.Web, Sophos, OpenPhish, URLhaus, Google Safe Browsing, etc.) and are collecting additional evidence (HTML, JS, network logs) for analysts. If you need any specific artifacts or exact timestamps from our audit logs, I can provide them via a secure channel.
Metadata
Metadata
Assignees
Labels
Type
Projects
Status