-
Notifications
You must be signed in to change notification settings - Fork 221
Extract unrelated code fixes/features out of k8s native apply work #196
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Extract unrelated code fixes/features out of k8s native apply work #196
Conversation
|
I think we do need to add in blocking the user from using
If we do need to block the user from using |
There's a chance you might have been using a different zarf version. I believe this PR prevents you from using localhost as the ingress. EDIT: Nope.. I didn't realize Jeff pushed a new commit out a few hours ago specifically allowing localhost again. I agree with Andy, maybe should probably consider just disallowing it. |
|
So on the |
|
@jeff-mccoy You're right that When I use |
|
Yeah this was an issue we ran into before if I recall, why we switched everything to hard-coded |
|
I'm okay with allowing 127.0.0.1 and blocking localhost. Let's do that. Question: Once the rest of the native apply stuff is in, are we going to have to block 127.0.0.1 also? |
|
as of today yes, there may be some clever workaround, but I haven't found it yet. 😢 |
|
@RothAndrew made that change in the last commit |
|
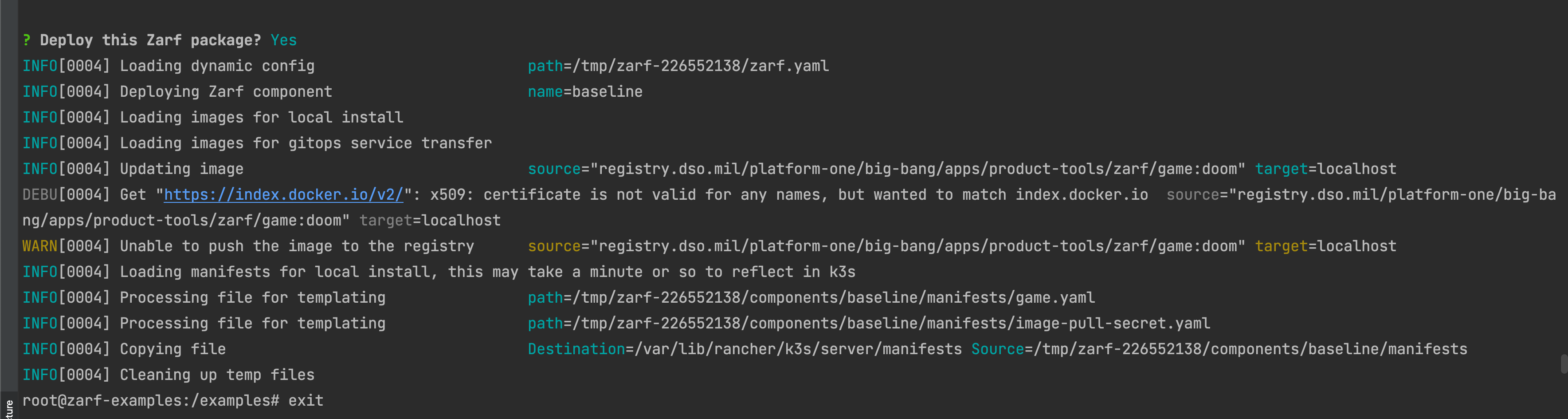
For some reason, in the Big Bang example, the Deploying the file with |
|
I changed the name of the file from |
|
that's super odd.... |
|
🤯 🤯 🤯 |
|
/test all |
|
/test all |
|
/test all |
|
hmm I thought we resolved these terraform versions issues already...also why do they keep popping up? I've never seen so many issues with terraform versions before. 😭 |
|
We can loosen up the version constraint. It is very restrictive right now. |
|
/test all |
|
As soon a Jeff pushes up the fix to remove |
|
I'm not sure how it's possible that the E2E tests are passing if we aren't using |
|
/test all |
|
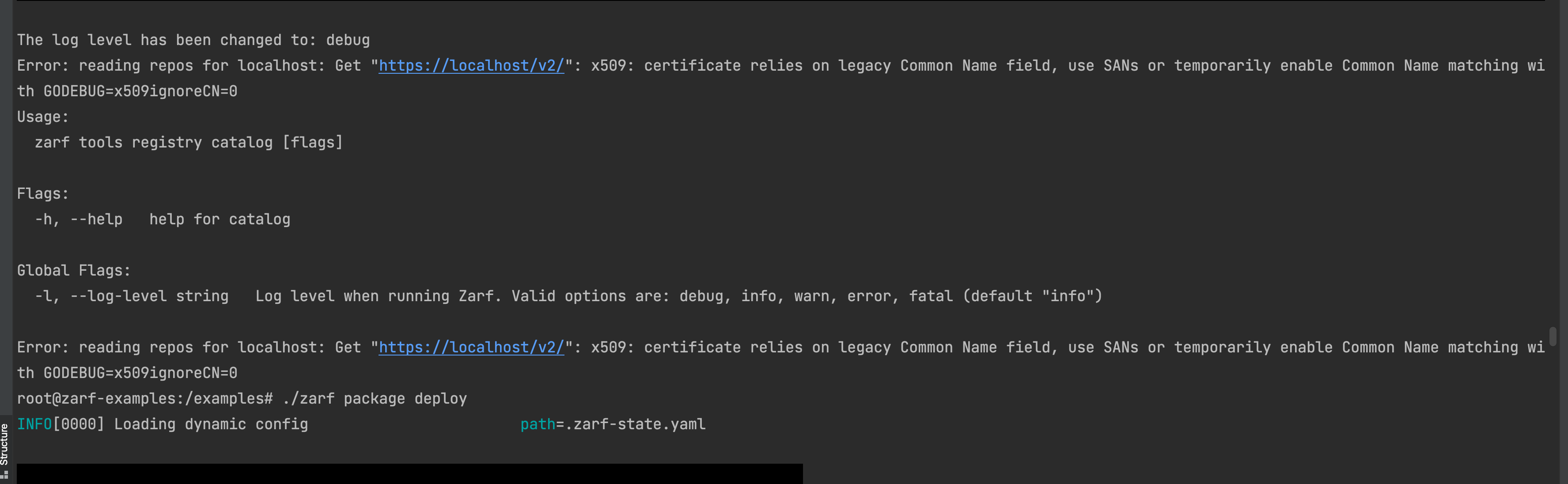
I'm still being prompted to choose whether to generate the CA or to import one when running |
Okay let me look at this |
|
oh weird its a race condition |
|
If you let it sit there it will keep running |
|
crap I remember now, I was supposed to put a top-level confirm box but forgot to.... ugh |
|
/test all |
|
/test all |
|
........and now registry1 auth is down lol |
|
Yep, that was my signal to quit for the night :D |
|
Okay I'm done with the PR now, all tests pass and I set it to squash/automerge whenever you guys get back to work. I'm going to pick back up my other work later tonight and reconcile against this branch even if it doesn't get merged until next week. Thanks for all the coordination, #teamworkMakesTheDreamWork. |
) ### Breaking Changes: * `localhost` is no longer a valid option for cluster ingress when initializing a zarf cluster. Instead you have to use a `127.0.0.1` or some other local ip found via `ifconfig` ### Fixes: * No longer depends on 127.0.0.1 local bindings for the registry / gitops service * should fix #193 * Resolve outstanding issues with image hostname swapping and * fixes #18 * fixes #44 * fixes #194 ### Features: * Adds `before` and `after` script options when defining a `zarf.yaml` with an optional retry flag * Add symlink to ZarfFile for creating links to places files * Add template boolean to ZarfFile to allow injection of zarf variables into text files * Adds a new `zarf tool` command to print out config schema and commit the output to the repo (will need to make a git hook or something later on) * Changes `zarf destroy` command to run any script that starts with `zarf-clean` instead of only running the k3s-remove script * Add new ZarfState and `.zarf-state.yaml` for persisting host information from `zarf init` to `zarf package deploy` * Remove all hard-coded logic for k3s install, now uses only standard zarf component features like everything else * Add user prompt with host/IP address suggestions for ingress #### Misc: * Upgrades k3s from v1.21.2 to v1.21.6 * Adds optional regex filter for when performing RecursiveFileList() * Adds more description to the components in zarf.yaml * Renames type ZarfConfig to ZarfPackage in the config pkg * Handful of general code organizing changes (moving yaml related functions to the `...../utils/yaml.go`, etc.) * Expose execCommand() with stdout control * Move traefik to standalone component and drop the internal k3s install of traefik * Use the airgap tarball of K3s instead of manually listing images * Cleanup init prompt logic Signed-off-by: Jeff McCoy <[email protected]>
) ### Breaking Changes: * `localhost` is no longer a valid option for cluster ingress when initializing a zarf cluster. Instead you have to use a `127.0.0.1` or some other local ip found via `ifconfig` ### Fixes: * No longer depends on 127.0.0.1 local bindings for the registry / gitops service * should fix #193 * Resolve outstanding issues with image hostname swapping and * fixes #18 * fixes #44 * fixes #194 ### Features: * Adds `before` and `after` script options when defining a `zarf.yaml` with an optional retry flag * Add symlink to ZarfFile for creating links to places files * Add template boolean to ZarfFile to allow injection of zarf variables into text files * Adds a new `zarf tool` command to print out config schema and commit the output to the repo (will need to make a git hook or something later on) * Changes `zarf destroy` command to run any script that starts with `zarf-clean` instead of only running the k3s-remove script * Add new ZarfState and `.zarf-state.yaml` for persisting host information from `zarf init` to `zarf package deploy` * Remove all hard-coded logic for k3s install, now uses only standard zarf component features like everything else * Add user prompt with host/IP address suggestions for ingress #### Misc: * Upgrades k3s from v1.21.2 to v1.21.6 * Adds optional regex filter for when performing RecursiveFileList() * Adds more description to the components in zarf.yaml * Renames type ZarfConfig to ZarfPackage in the config pkg * Handful of general code organizing changes (moving yaml related functions to the `...../utils/yaml.go`, etc.) * Expose execCommand() with stdout control * Move traefik to standalone component and drop the internal k3s install of traefik * Use the airgap tarball of K3s instead of manually listing images * Cleanup init prompt logic Signed-off-by: Jeff McCoy <[email protected]>
Breaking Changes:
localhostis no longer a valid option for cluster ingress when initializing a zarf cluster. Instead you have to use a127.0.0.1or some other local ip found viaifconfigFixes:
Features:
beforeandafterscript options when defining azarf.yamlwith an optional retry flagzarf toolcommand to print out config schema and commit the output to the repo (will need to make a git hook or something later on)zarf destroycommand to run any script that starts withzarf-cleaninstead of only running the k3s-remove script.zarf-state.yamlfor persisting host information fromzarf inittozarf package deployMisc:
...../utils/yaml.go, etc.)