|
1 | 1 | # Security Features |
2 | 2 |
|
3 | | -Devtron’s tool is also providing you `Security Features` to identify the vulnerabilities inside your code and to protect your code from external attacks. |
| 3 | +Devtron provides strong security features that help identify vulnerabilities in container images. The system scans container images thoroughly and generates reports if any vulnerabilities are found. |
4 | 4 |
|
5 | | -The system will scan your code and inform you if there are any Vulnerabilities present in your code. Also to make this feature more flexible to use, we have added a capability using which you can whitelist or block any vulnerability, and your code will be scanned considering the defined whitelist or blocked vulnerabilities. |
| 5 | +Within the CI pipeline of Devtron, there is an option called [**Scan for vulnerabilities**](creating-application/workflow/ci-pipeline.md#scan-for-vulnerabilities). |
6 | 6 |
|
7 | | -Remember, we discussed the [Scan for vulnerabilities](creating-application/workflow/ci-pipeline.md#scan-for-vulnerabilities) option in the CI pipeline. You can enable this feature from the CI Pipeline page. The system will scan your code and will show you all vulnerabilities present in your code. |
| 7 | + |
8 | 8 |
|
9 | | -We have created `Security features` to identify the vulnerabilities inside your code and to protect you from external attacks. |
| 9 | +By enabling this option, the system automatically scans the container image after the image build stage. It then generates a report that highlights all the vulnerabilities present within the image. To access the scan report of all builds with vulnerability scans enabled, simply navigate to the 'Security' tab on the dashboard. There you can conveniently view the build history and all the vulnerabilities detected in the build image. |
10 | 10 |
|
11 | | -This Security Feature has two processes: |
| 11 | + |
12 | 12 |
|
13 | | -1. Scanning |
14 | | -2. Policy |
| 13 | +The scan report provides a comprehensive overview of any vulnerabilities present in the image. This allows you to identify and address potential security risks effectively. By leveraging this feature, you can ensure that your containerized applications are safeguarded against known vulnerabilities. |
15 | 14 |
|
16 | | -## Scanning |
| 15 | +Devtron's Security Feature consists of two primary components: |
17 | 16 |
|
18 | | -This process starts executing after the successful execution of the CI pipeline and before the deployment\(CD\) process starts. |
| 17 | +1. **Security Scans** |
| 18 | +2. **Security Policies** |
19 | 19 |
|
20 | | -It scans your code to find any potential threat and shows you the list of vulnerabilities as an output of the CI pipeline if it finds any. |
| 20 | +## Security Scans |
21 | 21 |
|
22 | | -We will discuss later how you will see the list of your found vulnerabilities. |
| 22 | +Devtron's security scans provide comprehensive scan reports for all applications that have undergone vulnerability scanning. These reports offer a detailed overview of the security status of each scanned application. |
23 | 23 |
|
24 | | -## Policy |
| 24 | +These comprehensive scan reports provide valuable insights, including information about identified vulnerabilities, their severity levels, and any corresponding Common Vulnerabilities and Exposures (CVE) entries. |
25 | 25 |
|
26 | | -Vulnerabilities have different levels like Critical, Moderate, and Low. Users can define policy according to the level of vulnerability. Users can also block the vulnerability or allow\(whitelist\) the vulnerability for their code. |
| 26 | +## Security Policies |
27 | 27 |
|
28 | | -If any vulnerability is found which is blocked by the user, then it will not deploy the application. And if it finds any vulnerability which is whitelisted by the user, then the build image can be deployed. |
| 28 | +Devtron's Security Policies feature allows users to define policies based on the severity levels of vulnerabilities, which include `Critical`, `Moderate`, and `Low`. Users have the flexibility to set policies that either block the deployment of container images with vulnerabilities or allow their deployment. |
29 | 29 |
|
30 | | -The user gets informed in both cases if it finds any vulnerability or doesn't find any. |
| 30 | +With this feature, users can specify their desired actions for each severity level. For example, they can choose to block any container image with `Critical` vulnerabilities, while allowing container images with `Moderate` or `Low` vulnerabilities to be deployed. |
31 | 31 |
|
32 | | -**How to Check Vulnerability** |
| 32 | +### Checking Comprehensive Vulnerability Scan Report |
33 | 33 |
|
34 | | -You can find the Vulnerabilities `Build History` Page if you have enabled the `Scan for vulnerabilities` option. |
| 34 | +To access the comprehensive security scan reports, follow these steps: |
35 | 35 |
|
36 | | -Your Application-> Build History-> Select pipeline-> Go to Security Tab. |
| 36 | +1. Navigate to the `Security` tab within Devtron. |
| 37 | +2. Select the desired application from the available list. |
37 | 38 |
|
38 | | - |
| 39 | + |
39 | 40 |
|
40 | | -Here you can see all the vulnerabilities found in the build image. |
| 41 | +This action will provide detailed information regarding the security scan of the application, including the CVE, Severity of the identified vulnerabilities, as you can see in the image below. |
41 | 42 |
|
42 | | -Every vulnerability has `CVE ID`, `Severity Level`, Package, Current Version, and Fixed In Version. |
| 43 | + |
43 | 44 |
|
44 | | -**CVE ID**- Common Vulnerability ID |
| 45 | +Each vulnerability is identified by a **CVE ID** and categorized based on **Severity**, **Package**, **Current Version**, and **Fixed In Version**. |
45 | 46 |
|
46 | | -**Severity Level**- informs you about the severity of the vulnerability, it is defined as Critical, Medium, and Low. |
| 47 | +* **`CVE ID`** refers to the Common Vulnerability ID assigned to each vulnerability. |
| 48 | +* **`Severity`** indicates the severity of the vulnerability and can be classified as Critical, Medium, or Low. |
| 49 | +* The **`Package`** column contains metadata associated with the vulnerability. The current Version refers to the specific version of the vulnerability. |
| 50 | +* The **`Fixed In Version`** column displays the version name if the vulnerability has been addressed in a subsequent release; otherwise, it remains blank. |
47 | 51 |
|
48 | | -**Package**- column contains some meta-data of vulnerability. |
| 52 | +### Discover Vulnerabilities on the Trigger Page |
49 | 53 |
|
50 | | -**Current Version**- is the version of that vulnerability |
| 54 | +Devtron provides the capability to identify vulnerabilities before image deployment in the Continuous Deployment (CD) pipeline. This ensures that potential vulnerabilities are detected and addressed early in the deployment process. |
51 | 55 |
|
52 | | -**Fixed In Version**- column contains version name if it has been fixed in any version, else it remains blank |
| 56 | +To access security vulnerability details during image deployment in Devtron, follow these steps: |
53 | 57 |
|
54 | | -**Find Vulnerabilities on the Trigger Page** |
| 58 | +1. Click on the `Show source info` option for the desired image during the deployment process. |
| 59 | +2. Navigate to the `Security` tab. |
55 | 60 |
|
56 | | -You can find Vulnerabilities on the `Trigger` page also. Image having vulnerabilities will be marked as `Security Issues Found` and you won’t be able to select the image to deploy it. |
| 61 | + |
57 | 62 |
|
58 | | -You can see details of these vulnerabilities by expanding the `Show Source Info`. |
| 63 | +In the `Security` tab, you will find the security vulnerability details associated with the image. |
59 | 64 |
|
60 | | -See the below image. |
| 65 | +**NOTE**: Vulnerabilities will only be displayed if a vulnerability scan has been enabled for that specific image. If no vulnerabilities are visible, it indicates that a vulnerability scan has not been performed for the image. |
61 | 66 |
|
62 | | - |
| 67 | +### Accessing Vulnerability Information on the App Details Page |
63 | 68 |
|
64 | | -Click on the `Show Source Info` option. A window will be expanded with two options- Changes and Security. Click on the Security tab to view details about the vulnerabilities in the code. |
| 69 | +Devtron offers the capability to identify vulnerabilities even after an image has been deployed. By navigating to the `app details` page, you can find comprehensive details about the vulnerabilities associated with the deployed image. |
65 | 70 |
|
66 | | - |
| 71 | +With this capability, Devtron empowers users to stay informed about the security vulnerabilities present in their deployed images. |
67 | 72 |
|
68 | | -**Find Vulnerabilities on the App Details Page** |
| 73 | + |
69 | 74 |
|
70 | | -You can find Vulnerabilities on the `App Details` page too. Here we are displaying the total number of vulnerabilities found in the code and their Severity Level wise segregation. |
| 75 | +By clicking on the 'Details' link in the security vulnerabilities report, you can access detailed information about the security vulnerabilities present inside the deployed image. |
71 | 76 |
|
72 | | - |
| 77 | +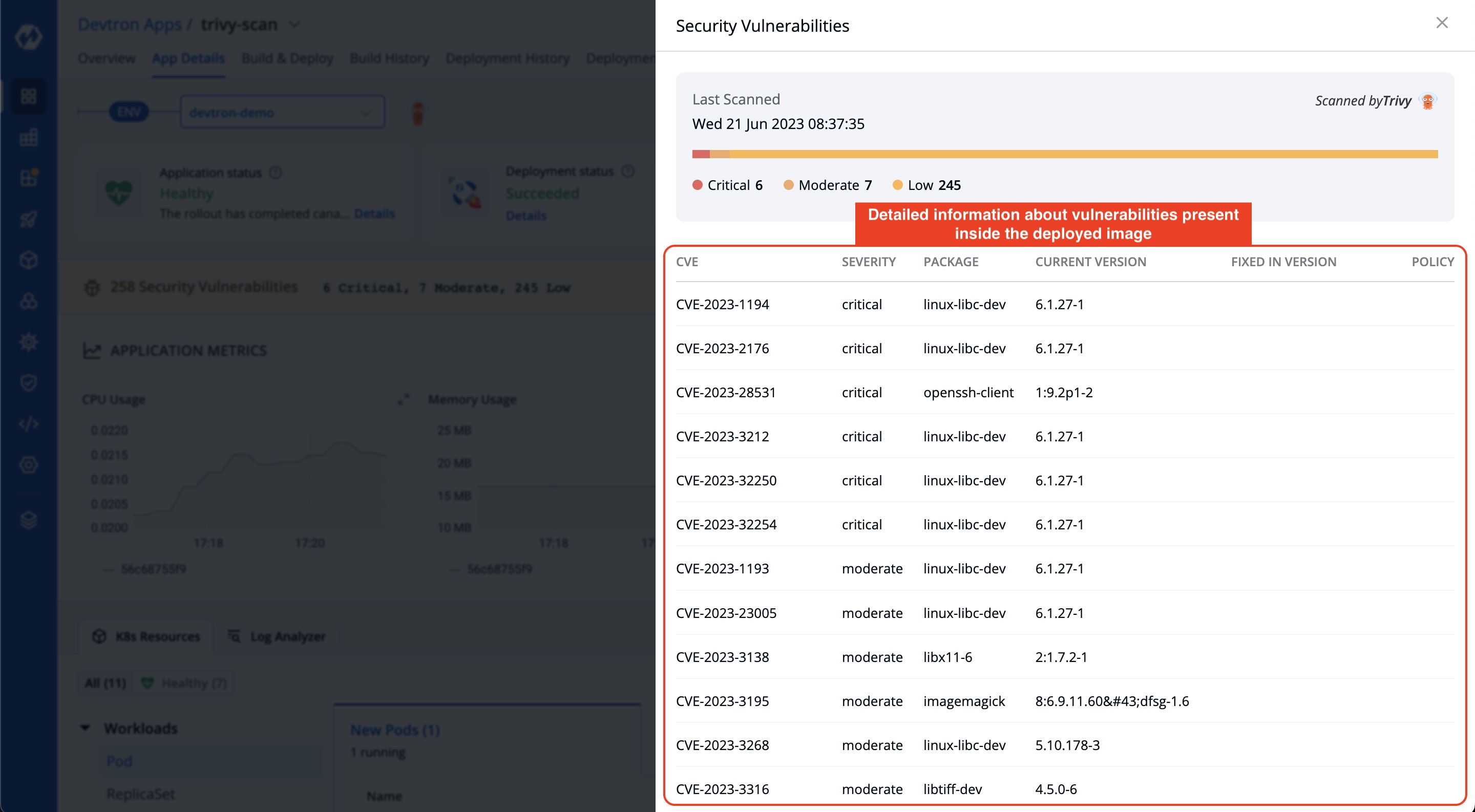 |
73 | 78 |
|
74 | | -## Security |
| 79 | +## Configuring Security Policies |
75 | 80 |
|
76 | | -You can check Vulnerabilities for all your applications in one place. On the Home page, there is an option named `Security`. Here, you can see a list of applications under the `Security Scan` tab. Here all the applications are listed which have the `Scan for Vulnerabilities` feature enabled. You can see the vulnerability count along with the Severity Level for all your applications. |
| 81 | +You can establish security policies for their vulnerabilities through the `Security Policies` tab, which can be accessed from the left pane by navigating to `Security` and selecting `Security Policies`. Policies are implemented in a hierarchical order, following a specific sequence. The order of implementation is as follows, starting from the highest level: |
77 | 82 |
|
78 | | -**Note:-** |
| 83 | +* **Global** |
| 84 | +* **Cluster** |
| 85 | +* **Environment** |
| 86 | +* **Application** |
79 | 87 |
|
80 | | -It displays the “Vulnerability count and Severity Level” on a priority basis. And critical level has the highest priority, so it displays the critical level vulnerabilities and there counts if any application is having critical vulnerability in it. |
| 88 | +Policies are implemented in a hierarchical order, with the following sequence: Global, Cluster, Environment, and Application. Higher-level policies take precedence over lower-level policies, ensuring a systematic and structured enforcement of security measures. |
81 | 89 |
|
82 | | -You can directly `Search` your application using the Search bar or you can `filter out` your requirement according to Severity, Clusters, and Environment. |
83 | | - |
84 | | - |
85 | | - |
86 | | -Now if you click on the severity level of vulnerability it will show you the list of all vulnerabilities along with other details. |
87 | | - |
88 | | - |
89 | | - |
90 | | -## Security Policies: |
| 90 | + |
91 | 91 |
|
92 | | -Users can define Security policies for their vulnerabilities under `Security Policies` Tab. |
| 92 | +**Some examples of how policies can be defined** |
93 | 93 |
|
94 | | -Home Page-> Security - > Security Policies |
| 94 | +Users can block all the critical vulnerabilities and allow the moderate and low vulnerabilities <br /> |
| 95 | +or <br /> |
| 96 | +Users can block all vulnerabilities <br /> |
| 97 | +or <br /> |
| 98 | +Users can block all vulnerabilities for one application and can block only critical vulnerabilities for other applications |
95 | 99 |
|
96 | | -Policies can be defined to different levels- |
| 100 | +## Configure Global Security Policy |
97 | 101 |
|
98 | | -* Global |
99 | | -* Cluster |
100 | | -* Environment |
101 | | -* Application |
| 102 | +Within the `Global Security Policies`, there are two options available: Block and Allow. |
| 103 | +If critical severity levels are blocked in the `Global Security Policy`, the same blocking will be applied to the `Cluster Security Policy`. Similarly, if the global policy is modified to allow critical levels, it will also allow them in `Cluster Security Policies`. |
| 104 | +However, users have the flexibility to explicitly modify these policies as desired. |
102 | 105 |
|
103 | | -**Note:-** |
| 106 | + |
104 | 107 |
|
105 | | -Policies work in hierarchical order. |
| 108 | +## Configure Cluster Security Policy |
106 | 109 |
|
107 | | -Order to be followed- First Global and second Cluster and so on as you can see the order of the options |
108 | 110 |
|
109 | | - |
| 111 | +In `Global Security Policies`, there are two options: `Block` and `Allow`. `Cluster Security Policies` have an additional option called `Inherit`. |
110 | 112 |
|
111 | | -**Some examples of how policies can be defined** |
| 113 | +When `Inherit` is selected, the policy adopts settings from higher-level options. For example, if critical severity levels are blocked globally, they will also be blocked in `Cluster Security Policies`. Changing the global policy to allow critical levels will also allow them in `Cluster Security Policies`. Explicit changes can be made to these policies. |
112 | 114 |
|
113 | | -Users can block all the critical vulnerabilities and allow the moderate and low vulnerabilities or Users can block all vulnerabilities or users can block all vulnerabilities for one application and can block only Critical vulnerabilities for other applications. |
| 115 | +To block critical vulnerabilities globally but allow them in specific clusters: |
114 | 116 |
|
115 | | -## Configure Global Policy |
| 117 | +1. Select the desired cluster. |
| 118 | +2. Change the critical setting to allow. |
| 119 | +3. This change only affects the policy of the selected cluster without impacting others or the global policy. |
116 | 120 |
|
117 | | -To configure these policies, click on the drop-down option of the severity levels and select Block or Allow. |
| 121 | + |
118 | 122 |
|
119 | | - |
| 123 | +## Configure Environment Security Policy |
120 | 124 |
|
121 | | -## Configure Cluster Security Policy |
| 125 | +Environment Security Policies, like Cluster Security Policies, offer three options: Block, Allow, and Inherit. |
122 | 126 |
|
123 | | -In the Global Security Policies, there are only two options available- Block and Allow. But in other options, we have an extra option named `Inherit`. |
| 127 | +The `Environment Security Policy` inherits its settings from the `Cluster Security Policy`, following a hierarchical structure where each level inherits the policy from its upper level. |
124 | 128 |
|
125 | | -As the name itself gives you an idea about this option, it fetches the policy of its upper-level options, if we choose to inherit in the drop-down. |
| 129 | +When you select an environment, it automatically adopts the policy of the associated cluster. For example, if critical-level vulnerabilities are blocked globally but allowed in the `Cluster Security Policy`, the `Environment Security Policy` will inherit this allowance. Consequently, critical-level vulnerabilities will also be allowed in the `Environment Security Policy`. |
126 | 130 |
|
127 | | -Example-if you block critical severity levels in Global, then critical levels will be blocked in Cluster Security Policy. In case we change critical policy globally and allow it there, then it will be allowed in Cluster Security Policies too. But you can change these policies explicitly. |
| 131 | +However, you have the flexibility to make explicit changes to the policy if needed. This empowers you to customize the policy to align with specific requirements or preferences. |
128 | 132 |
|
129 | | -If you want to block Critical Vulnerabilities in Global Security Policies but want to allow them in some clusters, then select your cluster and change the critical drop-down to allow. It will not affect the policy of other clusters and global also. |
| 133 | + |
130 | 134 |
|
131 | | -## Configure Environment Security Policy |
| 135 | +## Configure Application Security Policy |
132 | 136 |
|
133 | | -Again we have three options to define a policy- Block, Allow, and Inherit. |
| 137 | +The `Application Security Policy` operates on a similar principle as other policies. However, in the `Application Security Policy`, the policy is determined by both the Environment option and the Application option. |
134 | 138 |
|
135 | | -Environment Security Policy inherits the policy from Cluster Security Policy. Each level inherits the policy of its upper level. |
| 139 | +When modifying the policy within a development environment, the changes will be applied to all applications within that specific development environment. This means that any adjustments made to the policy settings will be consistently applied across all applications associated with that particular development environment. |
136 | 140 |
|
137 | | -Select any environment here, you will find it is inheriting the policy of Cluster. |
| 141 | +This approach ensures uniformity and streamlined management of security policies within specific environments and their corresponding applications. |
138 | 142 |
|
139 | | -Example- If you have blocked critical level vulnerabilities in Global Security Policy but allowed them in Cluster Security Policy, then Environment Security Policy will inherit the policy of cluster not global, Hence critical level vulnerabilities will be allowed in the Environment Security Policy. |
| 143 | + |
140 | 144 |
|
141 | | -Though, You can change the policy explicitly. |
| 145 | +## Block or Allow Specific CVE Policies. |
142 | 146 |
|
143 | | -## Configure Application Security Policy |
| 147 | +To block or allow specific Common Vulnerabilities and Exposures (CVE) policies, simply click `Add CVE Policy`. |
144 | 148 |
|
145 | | -The same thing goes with the `Application Security Policy`. But in Application, the policy is set with the combination of `Environment` option and `Application` option. If you change the policy in a dev environment that it will apply to all the applications which are in the `dev` environment. |
| 149 | +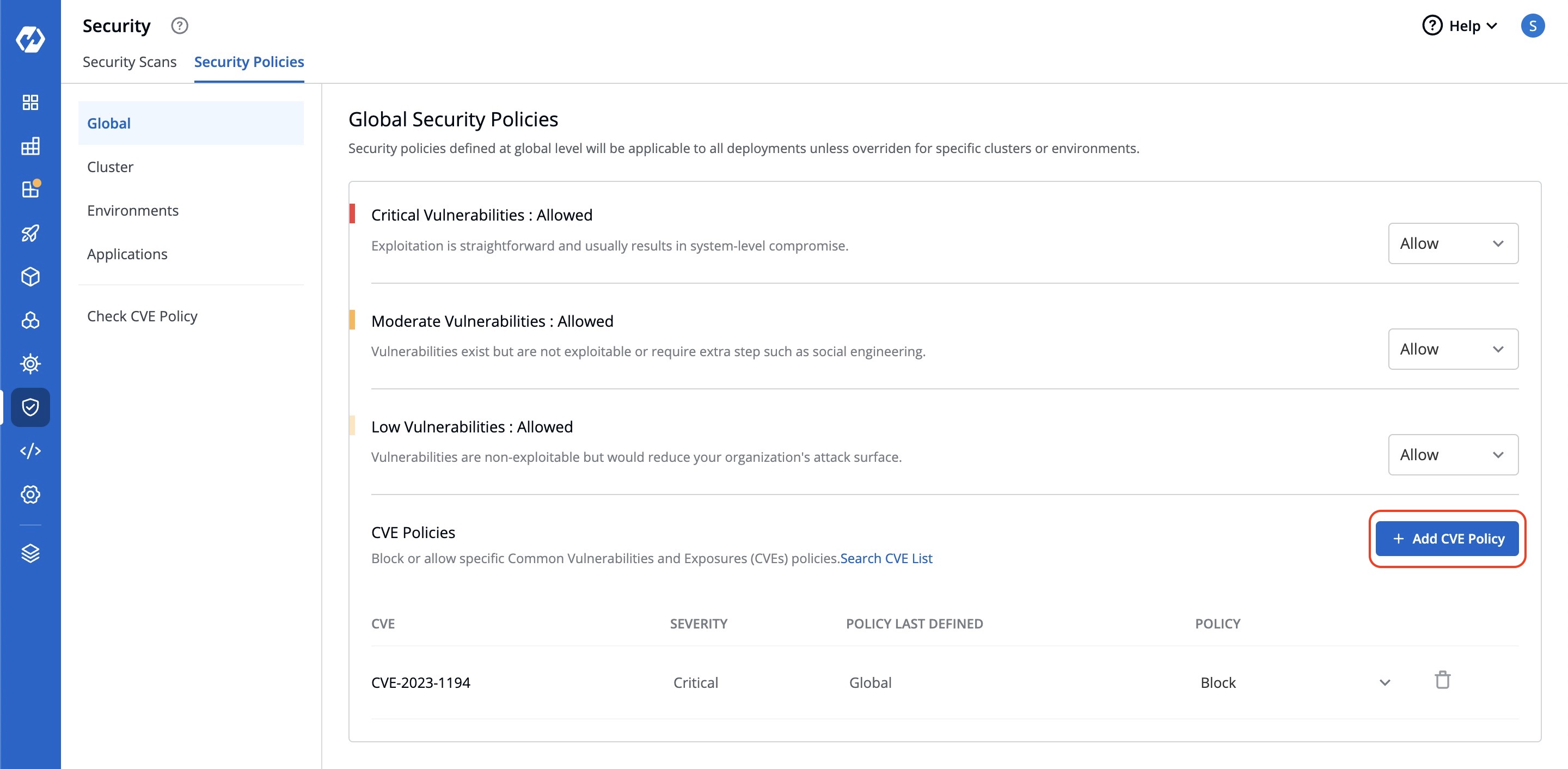 |
146 | 150 |
|
147 | | -## Check CVE Policy |
| 151 | +A window will appear where you can enter the CVE ID and select whether to allow or block it. |
148 | 152 |
|
149 | | -Here is the last option `Check CVE Policy`, If you want to configure a security policy specific to any Vulnerability, you can use this option. |
| 153 | + |
150 | 154 |
|
151 | | -Click on this option, it will show you a search bar, copy any CVE ID or vulnerability ID, and click on `Search`. It will display the details regarding that CVE ID and you can configure the policy to that particular CVE ID. |
| 155 | +This action will determine whether image deployment is allowed or blocked based on the presence of vulnerabilities matching that particular CVE ID. Any other deployment decisions will be made according to the policies set previously. |
152 | 156 |
|
0 commit comments