|
1 | 1 | # Clusters |
2 | 2 |
|
3 | | -Devtron’s tool is also providing you `Security Features` to identify the vulnerabilities inside your code and to protect your code from external attacks. |
| 3 | +As `Devtron` is a tool integration platform for Kubernetes, a [cluster](https://docs.devtron.ai/getting-started#create-a-kubernetes-cluster) is created as a pre-requisite before you install Devtron depending on your [resource usage and requirements](https://docs.devtron.ai/getting-started#recommended-resources). |
4 | 4 |
|
5 | | -The system will scan your code and inform you if there are any Vulnerabilities present in your code. Also to make this feature more flexible to use, we have added a capability using which you can whitelist or block any vulnerability, and your code will be scanned considering the defined whitelist or blocked vulnerabilities. |
| 5 | +By integrating into a Kubernetes cluster, Devtron helps you to deploy, observe, manage and debug the existing Helm apps in all your clusters. |
6 | 6 |
|
7 | | -Remember, we discussed the [Scan for vulnerabilities](creating-application/workflow/ci-pipeline.md#scan-for-vulnerabilities) option in the CI pipeline. You can enable this feature from the CI Pipeline page. The system will scan your code and will show you all vulnerabilities present in your code. |
| 7 | +On the left navigation of Devtron, select `Clusters`. You will find the list of clusters in this section which you have added under [Global Configurations > Clusters & Environments](https://docs.devtron.ai/global-configurations/cluster-and-environments). |
8 | 8 |
|
9 | | -We have created `Security features` to identify the vulnerabilities inside your code and to protect you from external attacks. |
| 9 | +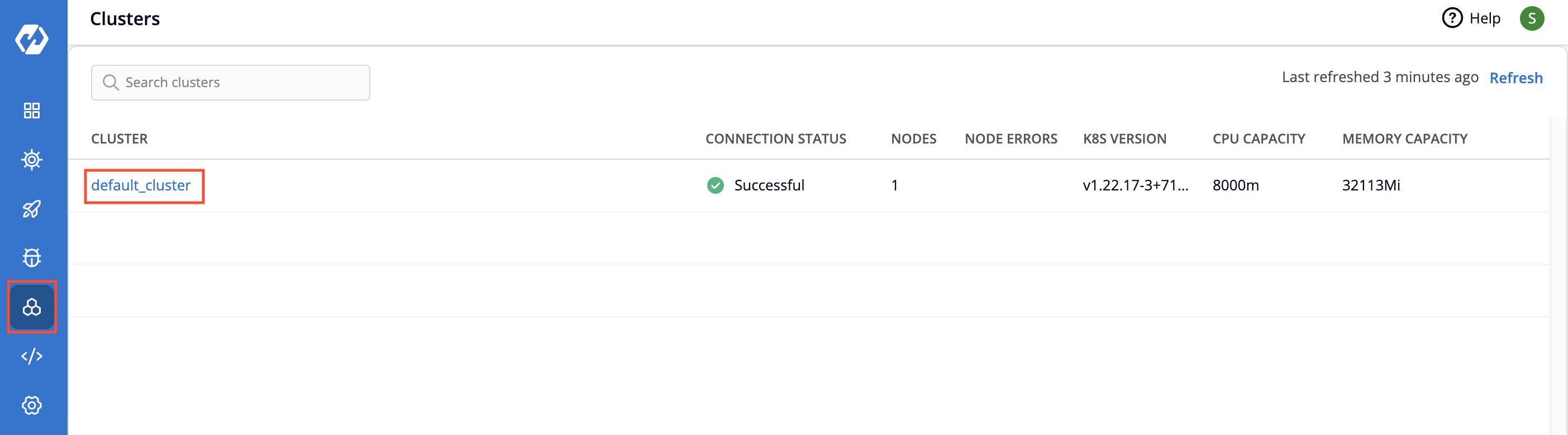 |
10 | 10 |
|
11 | | -This Security Feature has two processes: |
12 | 11 |
|
13 | | -1. Scanning |
14 | | -2. Policy |
| 12 | +| Fields | Description | |
| 13 | +| --- | --- | |
| 14 | +| **Cluster** | User-defined name for the cluster in Devtron. E.g. `default-cluster` | |
| 15 | +| **Connection Status** | Status of the cluster. The status can be either `Successful` or `Failed`. | |
| 16 | +| **Nodes** | Shows the number of nodes in a cluster. | |
| 17 | +| **Node Errors** | Shows the error in nodes. | |
| 18 | +| **K8s Version** | Shows the version of Kubernetes cluster. | |
| 19 | +| **CPU Capacity** | Shows the CPU capacity in your cluster in milicore. E.g., 8000m where 1000 milicore equals to 1 core. | |
| 20 | +| **Memory Capacity** | Shows the memory capacity in your cluster in mebibytes. | |
15 | 21 |
|
16 | | -## Scanning |
| 22 | +To see the details of resource allocation and usage of the cluster, click the particular cluster. |
17 | 23 |
|
18 | | -This process starts executing after the successful execution of the CI pipeline and before the deployment\(CD\) process starts. |
| 24 | +## Resources |
19 | 25 |
|
20 | | -It scans your code to find any potential threat and shows you the list of vulnerabilities as an output of the CI pipeline if it finds any. |
| 26 | +On the `Resource allocation and usage`, you can see the details of compute resources or resources. |
21 | 27 |
|
22 | | -We will discuss later how you will see the list of your found vulnerabilities. |
| 28 | +* CPU resources |
| 29 | +* Memory resources |
23 | 30 |
|
24 | | -## Policy |
| 31 | +If you specify a `request` and `limits` in the container resource manifest file, then the respective values will appear on the `Resource allocation and usage` section. |
25 | 32 |
|
26 | | -Vulnerabilities have different levels like Critical, Moderate, and Low. Users can define policy according to the level of vulnerability. Users can also block the vulnerability or allow\(whitelist\) the vulnerability for their code. |
| 33 | +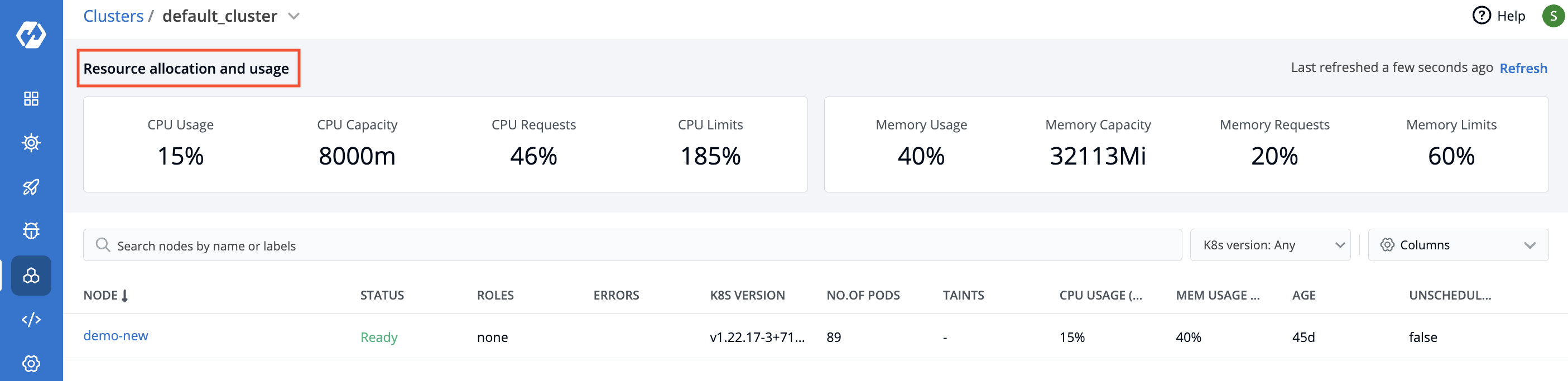 |
27 | 34 |
|
28 | | -If any vulnerability is found which is blocked by the user, then it will not deploy the application. And if it finds any vulnerability which is whitelisted by the user, then the build image can be deployed. |
| 35 | +## Nodes |
29 | 36 |
|
30 | | -The user gets informed in both cases if it finds any vulnerability or doesn't find any. |
| 37 | +You can see the list of nodes available in your cluster. Typically you have several nodes in a cluster; in a learning or resource-limited environment, you might have only one node. |
31 | 38 |
|
32 | | -**How to Check Vulnerability** |
| 39 | +The components on a typical node include the `kubelet`, a `container runtime`, and the `kube-proxy`. |
33 | 40 |
|
34 | | -You can find the Vulnerabilities `Build History` Page if you have enabled the `Scan for vulnerabilities` option. |
| 41 | +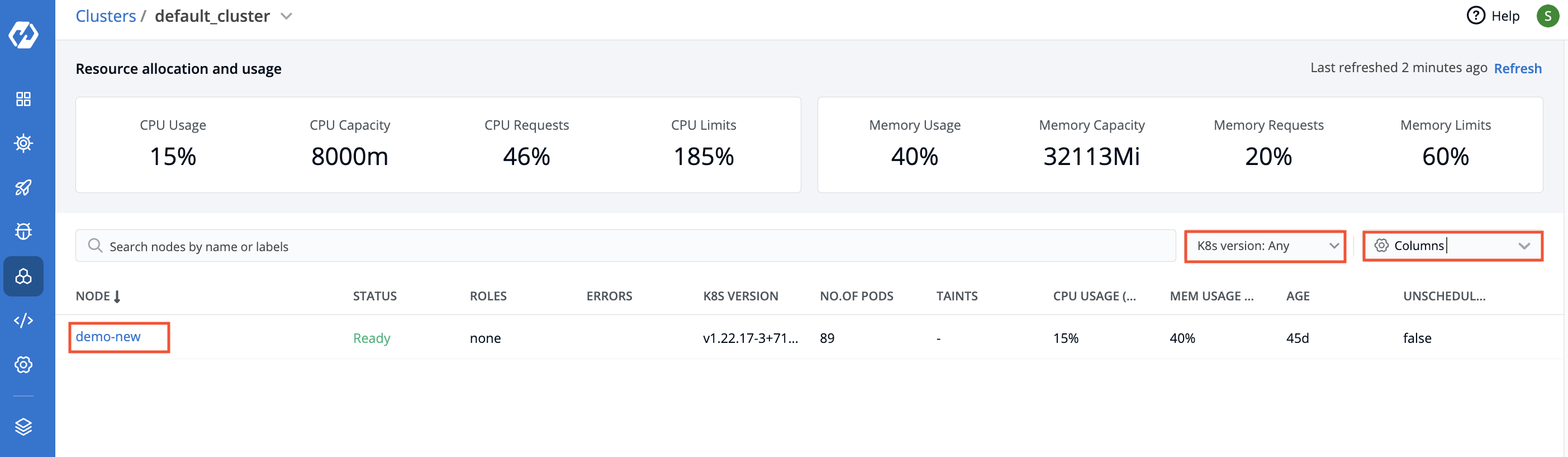 |
35 | 42 |
|
36 | | -Your Application-> Build History-> Select pipeline-> Go to Security Tab. |
| 43 | +If you have multiple nodes, you can search a node by name or label in the search bar. |
37 | 44 |
|
38 | | - |
| 45 | +| Fields | Description | |
| 46 | +| --- | --- | |
| 47 | +| **Node** | User-defined name for the node in Devtron. E.g. `demo-new`.<br>Note: Two nodes cannot have the same name at the same time.</br> | |
| 48 | +| **Status** | Status of a node. It can be either `Ready` or `Not Ready`. | |
| 49 | +| **Roles** | Shows the roles of a node. | |
| 50 | +| **Errors** | Shows the error in nodes. | |
| 51 | +| **K8s Version** | Shows the version of Kubernetes cluster. | |
| 52 | +| **No. of Pods** | Shows the number of namespaces or pods in a node. | |
| 53 | +| **CPU Usage** | Shows the CPU consumption in a node. | |
| 54 | +| **Mem Usage** | Shows the memory consumption in a node | |
| 55 | +| **Age** | Shows the time that the pod has been running since the last restart. | |
39 | 56 |
|
40 | | -Here you can see all the vulnerabilities found in the build image. |
| 57 | +To display a parameter of a node, use the `Columns` on the right side, select the parameter you want to display from the drop-down list and click `Apply`. |
41 | 58 |
|
42 | | -Every vulnerability has `CVE ID`, `Severity Level`, Package, Current Version, and Fixed In Version. |
| 59 | +To see the summary of a node, click the particular node. |
43 | 60 |
|
44 | | -**CVE ID**- Common Vulnerability ID |
| 61 | +## Troubleshoot Cluster via Terminal |
45 | 62 |
|
46 | | -**Severity Level**- informs you about the severity of the vulnerability, it is defined as Critical, Medium, and Low. |
| 63 | +User with [Super admins](https://docs.devtron.ai/global-configurations/authorization/user-access#assign-super-admin-permissions) access can now troubleshoot cluster issues by accessing the cluster terminal from Devtron. You can select an image from the list that has all CLI utilities like kubectl, helm, netshoot etc. or can use a custom image. |
47 | 64 |
|
48 | | -**Package**- column contains some meta-data of vulnerability. |
| 65 | +To troubleshoot a cluster or a specific node in a cluster, click the terminal symbol on the right side. |
49 | 66 |
|
50 | | -**Current Version**- is the version of that vulnerability |
| 67 | + |
51 | 68 |
|
52 | | -**Fixed In Version**- column contains version name if it has been fixed in any version, else it remains blank |
| 69 | +* You will see the user-defined name for the cluster in Devtron. E.g. `default-cluster`. |
| 70 | +* In the `Nodes` field, select the node from the drop-down list you want to troubleshoot. E.g. `demo-new`. |
| 71 | +* Select the namespace from the drop-down list which you have added in the [Environment](https://docs.devtron.ai/global-configurations/cluster-and-environments#add-environment) section. |
| 72 | +* Select the image from the drop-down list which includes all CLI utilities or you can use a custom image. |
| 73 | +* Select the terminal shell from the drop-down list (e.g. `sh`, `bash`, `powershell`, `cmd`) to troubleshoot a node. |
53 | 74 |
|
54 | | -**Find Vulnerabilities on the Trigger Page** |
55 | 75 |
|
56 | | -You can find Vulnerabilities on the `Trigger` page also. Image having vulnerabilities will be marked as `Security Issues Found` and you won’t be able to select the image to deploy it. |
57 | 76 |
|
58 | | -You can see details of these vulnerabilities by expanding the `Show Source Info`. |
59 | 77 |
|
60 | | -See the below image. |
61 | | - |
62 | | - |
63 | | - |
64 | | -Click on the `Show Source Info` option. A window will be expanded with two options- Changes and Security. Click on the Security tab to view details about the vulnerabilities in the code. |
65 | | - |
66 | | - |
67 | | - |
68 | | -**Find Vulnerabilities on the App Details Page** |
69 | | - |
70 | | -You can find Vulnerabilities on the `App Details` page too. Here we are displaying the total number of vulnerabilities found in the code and their Severity Level wise segregation. |
71 | | - |
72 | | - |
73 | | - |
74 | | -## Security |
75 | | - |
76 | | -You can check Vulnerabilities for all your applications in one place. On the Home page, there is an option named `Security`. Here, you can see a list of applications under the `Security Scan` tab. Here all the applications are listed which have the `Scan for Vulnerabilities` feature enabled. You can see the vulnerability count along with the Severity Level for all your applications. |
77 | | - |
78 | | -**Note:-** |
79 | | - |
80 | | -It displays the “Vulnerability count and Severity Level” on a priority basis. And critical level has the highest priority, so it displays the critical level vulnerabilities and there counts if any application is having critical vulnerability in it. |
81 | | - |
82 | | -You can directly `Search` your application using the Search bar or you can `filter out` your requirement according to Severity, Clusters, and Environment. |
83 | | - |
84 | | - |
85 | | - |
86 | | -Now if you click on the severity level of vulnerability it will show you the list of all vulnerabilities along with other details. |
87 | | - |
88 | | - |
89 | | - |
90 | | -## Security Policies: |
91 | | - |
92 | | -Users can define Security policies for their vulnerabilities under `Security Policies` Tab. |
93 | | - |
94 | | -Home Page-> Security - > Security Policies |
95 | | - |
96 | | -Policies can be defined to different levels- |
97 | | - |
98 | | -* Global |
99 | | -* Cluster |
100 | | -* Environment |
101 | | -* Application |
102 | | - |
103 | | -**Note:-** |
104 | | - |
105 | | -Policies work in hierarchical order. |
106 | | - |
107 | | -Order to be followed- First Global and second Cluster and so on as you can see the order of the options |
108 | | - |
109 | | - |
110 | | - |
111 | | -**Some examples of how policies can be defined** |
112 | | - |
113 | | -Users can block all the critical vulnerabilities and allow the moderate and low vulnerabilities or Users can block all vulnerabilities or users can block all vulnerabilities for one application and can block only Critical vulnerabilities for other applications. |
114 | | - |
115 | | -## Configure Global Policy |
116 | | - |
117 | | -To configure these policies, click on the drop-down option of the severity levels and select Block or Allow. |
118 | | - |
119 | | - |
120 | | - |
121 | | -## Configure Cluster Security Policy |
122 | | - |
123 | | -In the Global Security Policies, there are only two options available- Block and Allow. But in other options, we have an extra option named `Inherit`. |
124 | | - |
125 | | -As the name itself gives you an idea about this option, it fetches the policy of its upper-level options, if we choose to inherit in the drop-down. |
126 | | - |
127 | | -Example-if you block critical severity levels in Global, then critical levels will be blocked in Cluster Security Policy. In case we change critical policy globally and allow it there, then it will be allowed in Cluster Security Policies too. But you can change these policies explicitly. |
128 | | - |
129 | | -If you want to block Critical Vulnerabilities in Global Security Policies but want to allow them in some clusters, then select your cluster and change the critical drop-down to allow. It will not affect the policy of other clusters and global also. |
130 | | - |
131 | | -## Configure Environment Security Policy |
132 | | - |
133 | | -Again we have three options to define a policy- Block, Allow, and Inherit. |
134 | | - |
135 | | -Environment Security Policy inherits the policy from Cluster Security Policy. Each level inherits the policy of its upper level. |
136 | | - |
137 | | -Select any environment here, you will find it is inheriting the policy of Cluster. |
138 | | - |
139 | | -Example- If you have blocked critical level vulnerabilities in Global Security Policy but allowed them in Cluster Security Policy, then Environment Security Policy will inherit the policy of cluster not global, Hence critical level vulnerabilities will be allowed in the Environment Security Policy. |
140 | | - |
141 | | -Though, You can change the policy explicitly. |
142 | | - |
143 | | -## Configure Application Security Policy |
144 | | - |
145 | | -The same thing goes with the `Application Security Policy`. But in Application, the policy is set with the combination of `Environment` option and `Application` option. If you change the policy in a dev environment that it will apply to all the applications which are in the `dev` environment. |
146 | | - |
147 | | -## Check CVE Policy |
148 | | - |
149 | | -Here is the last option `Check CVE Policy`, If you want to configure a security policy specific to any Vulnerability, you can use this option. |
150 | | - |
151 | | -Click on this option, it will show you a search bar, copy any CVE ID or vulnerability ID, and click on `Search`. It will display the details regarding that CVE ID and you can configure the policy to that particular CVE ID. |
152 | 78 |
|
0 commit comments